Before we move ahead let me break the biggest myth of present times – Serverless Applications is servers on cloud and are to be managed by the cloud server providers. The term “Serverless” Applications gives an idea that administration of servers, which is one of the biggest headaches for IT teams, is not required. At […]
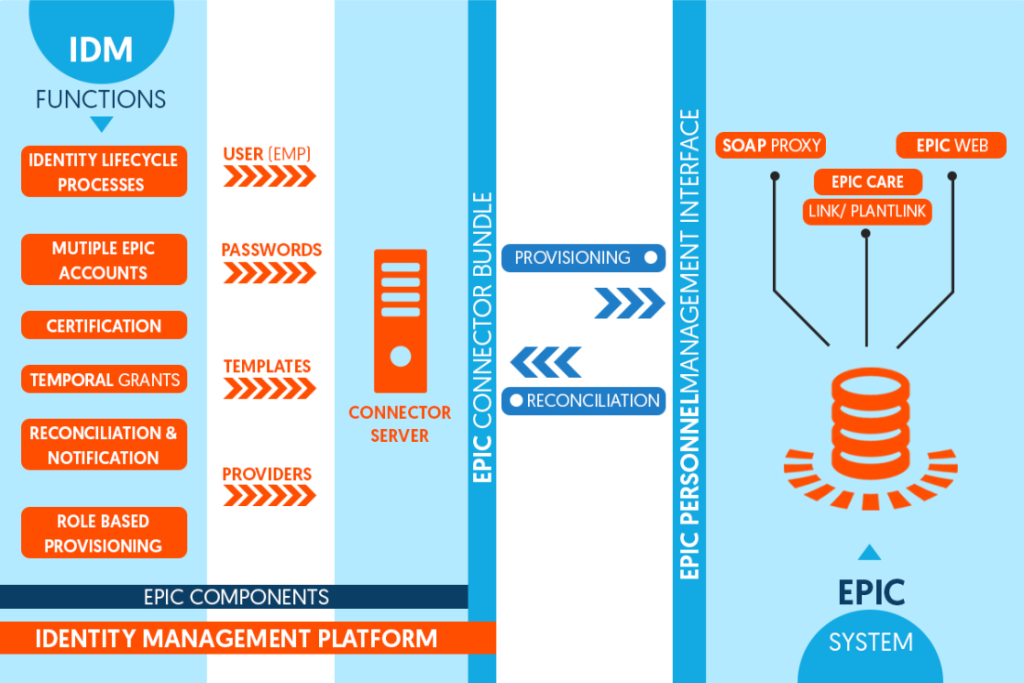
Impactful healthcare/hospital workflows depend on swift functioning of Electronic Medical Records (EMR) Systems such as EPIC, Cerner, Kronos, and other systems. These applications are created to bring ease in management of health records. However, many healthcare clients have shared challenges in managing identities and streamline accesses on EMR Systems. The source of this problem is […]
Are you facing challenges while managing identities on EPIC Systems in your organization? Typically, when an establishment relies too much on an application – strategic foresight in terms of aligning the application with business requirements needs to be just on the spot. Many healthcare establishments rely on EPIC Systems for the management of patient data, […]
I had an amazing discussion on my thoughts shared on Hybrid IT with few of you. One important challenge that was identified was unifying identities in a Hybrid setup. No doubt, identities drive IT processes in an enterprise setup, unification of identities thus becomes an important aspect of IT processes. Many a time, unifying identities […]
Technology is a disruptive game, we discover something new with each passing minute. Businesses are out in the race, they are ready to embrace technology to be closer to business goals, automation and achieve competitive advantage. However, this cannot ignore the security climate associated with new technologies. It is, therefore, important to study and visualize […]