
Secure and Streamline: The Future of Access Re-Certification
Access Re-Certification is crucial for ensuring your organization remains secure and compliant. This essential process involves regularly reviewing and validating user access to confirm that permissions align with current roles and responsibilities. By routinely assessing and updating access rights, you prevent unauthorized access, minimize security risks, and adhere to regulatory standards, ensuring users only have the access necessary for their job functions.
Understanding Access Re-Certification
Access Re-Certification systematically reviews user permissions to ensure they are still relevant and justified. Periodic evaluations align access rights with job roles, compliance requirements, and organizational policies. This proactive approach identifies and revokes outdated permissions, reducing the risk of security breaches and preventing over-privileged access.

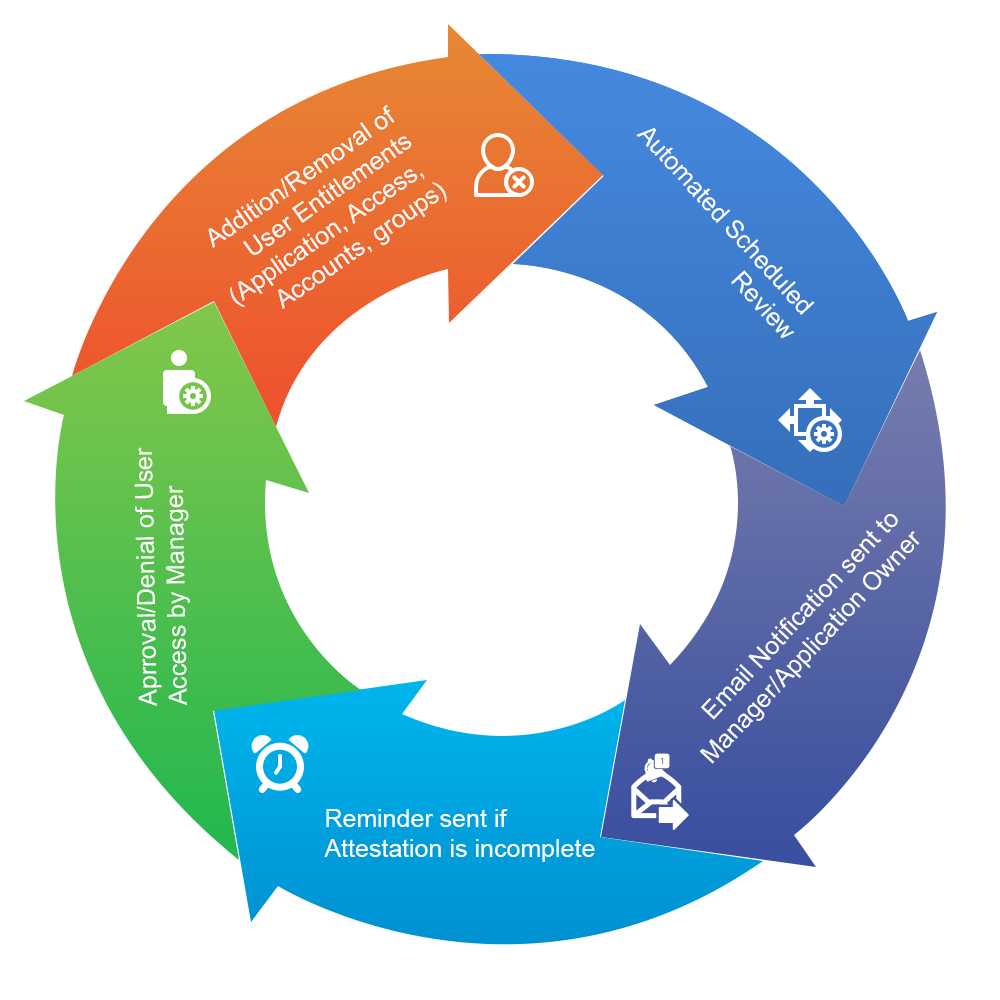
The Access Re-Certification Journey
In the dynamic environment of an enterprise, managing access rights throughout the user lifecycle is crucial. This process involves various stages such as the creation, updating, enabling, disabling, and transfer of user identities. Each identity is endowed with specific access privileges tailored to their respective roles within the organization.
- Identity Lifecycle Management
- Role-Based Access Control
- Continuous Monitoring
- Policy Enforcement
- Automated Workflows
By effectively managing the lifecycle of user identities and implementing robust access controls, organizations can ensure the security and integrity of their systems while facilitating efficient access management for their workforce.
Ensuring Security and Compliance
Effortless Access
Re-Certification Solutions
Access Re-Certification is a critical practice for maintaining robust security and regulatory compliance. By routinely validating user access permissions, organizations can mitigate risks, prevent unauthorized access, and ensure that access rights align with current roles and responsibilities.
Minimized Security Risks
- Regularly reviewing and updating user access helps prevent unauthorized access and reduces the risk of security breaches.
Enhanced Compliance
- Supports adherence to regulatory requirements by ensuring that only authorized individuals have access to sensitive information.
Improved Efficiency
- Reduces administrative overhead, allowing IT teams to focus on more critical tasks while maintaining accurate access control.
How Avancer Helps
Know how Avancer’s Access Re-Certification solution enhances and simplifies the re-certification process:
Automation
Streamlines the re-certification process with automated workflows and notifications.
Role-Based Evaluations
Supports focused assessments based on user roles and responsibilities.
Robust Audit Trail
Maintains a clear and detailed record for transparency and regulatory adherence.
Customizable Review Cycles
Tailors review schedules to meet your organization’s specific needs.
