
MFA: Security Beyond Passwords
Traditional security measures like firewalls and antivirus software are no longer sufficient to protect against sophisticated cyber threats. This is where Multi-Factor Authentication (MFA) comes into play, providing an essential layer of security that ensures only authorized users gain access to your digital assets. MFA, often referred to as 2FA (two-factor authentication), goes beyond the traditional single-factor authentication by requiring multiple forms of verification. This makes it exponentially more difficult for unauthorized users to breach your systems.
What is MFA?
Multi-Factor Authentication (MFA) is a vital security measure that requires multiple forms of verification to confirm a user's identity before granting access to a system, application, or data. Adding an extra layer of defense against unauthorized access, MFA combines two or more independent credentials: what the user knows (password), what the user has (security token), and what the user is (biometric verification).
Types of MFA:
MFA leverages multiple factors to verify the identity of users, categorized as follows:
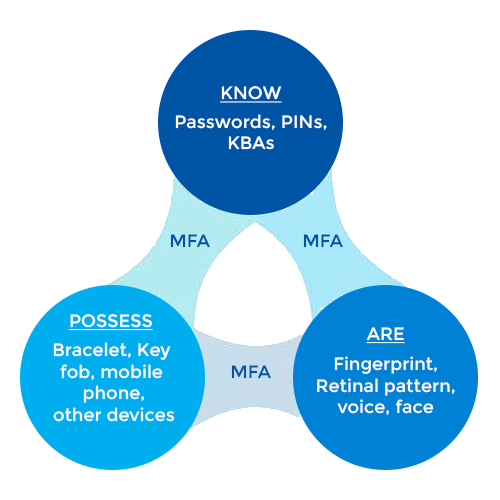
Majorly authentication factors are segregated into three types in MFA:
- Things You Know (Knowledge): Passwords, PINs
- Things You Possess (Physical Objects): Smartphones, Security Badges
- Things You Are (Inherence): Biometrics such as fingerprints, voice recognition
Additionally, there are other factors considered within the latest MFA solutions such as behavioral and contextual elements for authenticating.
- Location of the access request attempt – home/office/café
- What device is used for carrying out access request attempt – laptop/tablet/smartphone
- Time of access request attempt – during the workday/night
- Type of network used for access request attempt – public/private
How does MFA work?
Multi-Factor Authentication (MFA) verifies the identity of a user through multiple credentials, making it an essential component of Identity and Access Management (IAM) practices. Instead of relying solely on a username and password—which can be easily stolen or misused—MFA requires additional credentials such as one-time passwords (OTPs) sent to a smartphone or email, answers to security questions, facial recognition, fingerprints, and more.
Enhanced security through MFA significantly reduces the risk of brute force attacks. The multiple layers of authentication ensure that only legitimate users can access sensitive information and systems. By requiring additional verification steps, MFA effectively prevents unauthorized access, as attackers are unable to provide the necessary credentials, such as an OTP or biometric data.
The most common examples of MFA involve the following set of pairings for authentication:
- Fingerprints
- Codes/OTPs sent to an email address
- Smartphone app-generated codes
- Facial recognition
- Behavioral analysis
- Certificates and soft tokens
- Iris or retina scanning
- Barcode scanning
- Personal security question answer
- USB devices, badges, or other physical devices
Enhanced Security with Adaptive MFA
IAM Multi-Factor Authentication (MFA) offers cutting-edge Adaptive Authentication to elevate your security measures. MFA solution enhances security by identifying and responding to unusual login patterns. When a user attempts to authenticate from an unusual context—such as a new location or device—the system automatically triggers additional security protocols.
This adaptive approach requires extra credentials, ensuring an extra layer of protection and effectively safeguarding against unauthorized access. It not only strengthens security but also minimizes potential disruptions for legitimate users, providing a seamless and secure authentication experience.
Strengthen Cyber Defenses
Why MFA is a
Must-Have
By requiring multiple forms of verification, MFA strengthens security, reduces the risk of breaches, and adapts to unusual login patterns for dynamic protection. With MFA, safeguard your sensitive information and ensure a secure, seamless user experience.
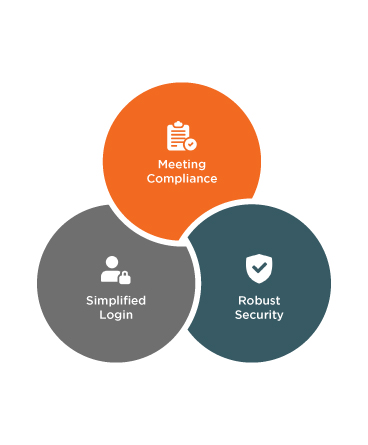
Enhanced Security
- Strengthens system security by adding multiple robust layers of protection, making unauthorized access exceedingly difficult.
Adaptive Authentication
- Intelligently adapts to login contexts and unusual patterns, dynamically adjusting security requirements while ensuring smooth access.
Ensure Compliance
- Meets industry regulations by safeguarding data, and ensuring compliance with data protection and privacy laws.
How Avancer Helps
Avancer provides comprehensive MFA solutions to enhance security and streamline processes.
Seamless Integration
Integrates seamlessly with existing IT systems and cloud platforms, ensuring minimal disruption and streamlined authentication.
Adaptive Authentication
Analyzes login contexts like device and location, adjusting security measures dynamically for robust protection against anomalies.
User-Centric Design
Designed for optimal usability, offering OTPs, biometrics, and security questions, balancing robust security with user convenience.
Risk Mitigation
Helps meet industry regulations and standards, protecting sensitive data and ensuring compliance with data protection laws.
