Avancer Corporation is a systems integrator focusing on State of Art Identity and Access Management technology. With over a decade of experience of integrating IAM solutions for world’s leading corporations we bring you some insights through our articles on Avancer Corporation’s Official Blog
For businesses such as banking, insurance, investment management and others belonging to the financial sector, managing security requirements becomes more and more challenging. Today, organizations are increasingly turning to cloud-based solutions to address their needs to reduce complexity, to ease scalability and to rapidly introduce new services to market.
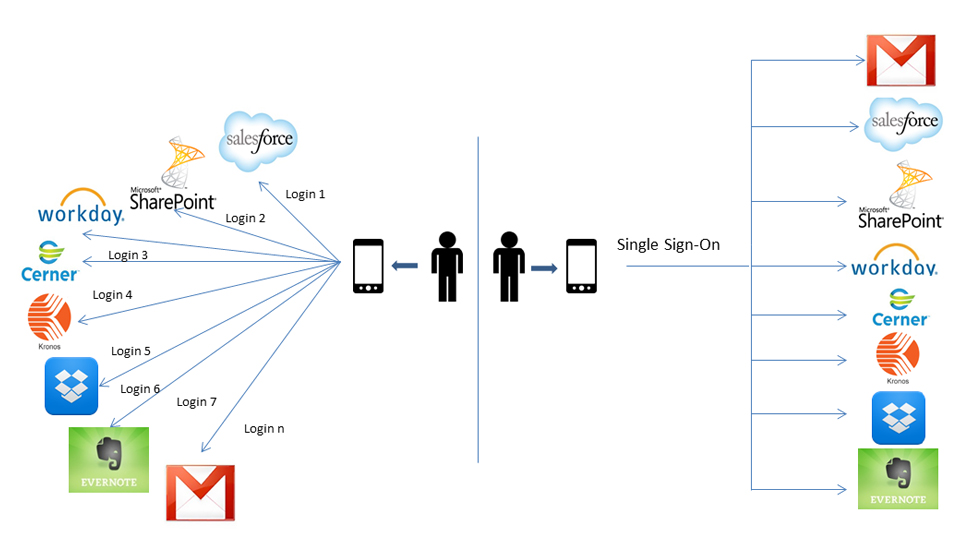
Among the various areas where cloud technology has proven to be a boon, Cloud Identity Management or Identity-as-a-service has become a crucial element for a comprehensive and effective data and resource security strategy.
Below are the benefits of this technology from the perspective of financial sector:
Time is Money
The company and clients can have access to important documents anytime and anywhere from any web-enabled device such as desktops, laptops, ... Read More